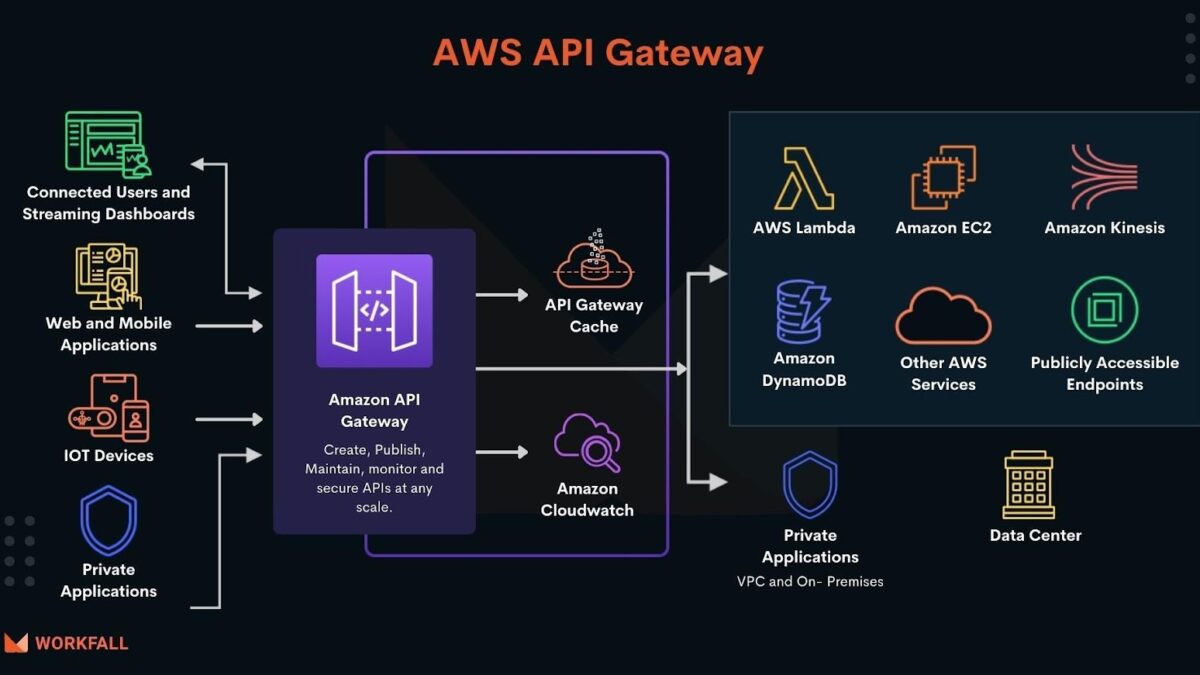
Application programming interfaces (APIs) enable the communication between two computer programs, thus enabling businesses to cooperate. Thanks to the API adoption, companies increased their market capitalization by 12.7% compared to those that haven’t introduced APIs.
In order to achieve such results yourself, you should build a secure and scalable API. Here are the most important steps you need to follow to do so.
Table of Contents
How to make a secure API
You’ll get instantly interested in API security once you learn this fact: a shocking 41% of businesses suffered some sort of an API security incident in 2021. Also, 63% of them complained about data loss or data breach.
For you to avoid such grim statistics, here’s what you need to do.
Use HTTPS at all times
This is hardly a mind-blowing suggestion, yet the consequences of not using it consistently can be rather serious. When you use SSL every time, you transform the authentication credentials into a randomly generated access token, thus making it stronger. That action takes the token to the HTTP Basic Auth username field.
In addition, you can use HTTP 2 for better performance. HTTP 2 can help you send a variety of requests over a single connection. Consequently, you’ll be avoiding the TCP and SSL handshake overhead in the follow-up requests.
Keep the URLs clean
Whatever you do, you shouldn’t let any passwords, API keys, usernames, or session tokens appear in the URL. That calls for an immediate data breach or data leak, and you won’t have anyone but yourself to blame for being so exploitable.
Hash the passwords
Hashing passwords will protect the system and minimize the hacking damage. Use hashing algorithms such as bcrypt, scrypt algorithms or PBKDF2 to improve password security. As hashing algorithms are one-way functions, no one else can decode or unscramble the text but you.
Switch to OAuth
In securing APIs, basic auth goes pretty much without saying, as it helps you reach a certain level of security. However, we’d rather you go beyond this and raise the API security bar with OAuth 2.0.
Why is OAuth so recommendable? Basically, this authorization framework can help a third-party application get limited HTTP service access. There are two ways to do this: either by allowing the third-party application to gain access on its own or on behalf of the resource owner by connecting the owner and the HTTP service.
Put a timestamp in the request
The main benefit of adding a timestamp as an HTTP custom header in API requests is that it’s going to prevent repeated cyber attacks. The server compares the current and request timestamps and only approves the request after a reasonable period (e.g., 30 seconds).
Validate request parameters
Use parameter validation at the very beginning, before a user reaches the application logic. Create strong validation checks whose failure will result in immediate request rejection.
Avoid unnecessary complex solutions
While setting up and maintaining API security is absolutely vital to the business, you should be careful not to overcomplicate your API security solutions. True, sometimes a complex solution is the only way, but the majority of the suggestions we’ve made are very straightforward, yet efficient. And in most cases, they suffice.
The more complex API solutions are, the higher the probability of overseeing something and leaving a “hole” in the system. That’s why you should try to keep it simple whenever possible.
How to make a Scalable API
API scalability is another determining growth factor in business. That’s the ability to deal with a continuous, sometimes heavy stream of requests without any issues with performance. This is particularly visible in e-commerce, where you can have an extensive and ever-growing customer base.
So, how do you scale an API to enable it to handle a multitude of different requests without any interruptions to the process? Here’s what you can do.
Make APIs stateless
Making an API stateless is important because, in that way, an API doesn’t require data from previous interactions — it’s already present in the incoming requests by design. Thanks to this feature, several servers can deal with a set request.
In contrast, a stateful API must access the information from previous sessions to complete a request.
Introduce asynchronous job processing
When you have a case where two or more operations don’t depend on each other, you can run them asynchronously, i.e., in parallel. This should enable you to complete bulk operations quickly. As a result, you’ll avoid long backlog lines in the system.
Regarding e-commerce, this feature is critical during the peak shipping season when bulk requests often occur and backlog queues are more prolonged.
Make use of hybrid NoSQL and SQL databases
To achieve better API scalability, we advise you to use both NoSQL and SQL databases, as you’re probably going to need both for efficient data management. For example, you should store faster read operations in an SQL database, while NoSQL databases are more suitable for heavier write operations. You just need to dynamically leverage which database is a better fit.
Regular control and timely (re)action
The above NoSQL should help you prevent any scaling bottlenecks, but it can’t be responsible for the overall API scalability. If you truly want to achieve optimal results, you’ll have to regularly monitor the load and alert internal teams if any issue occurs. Eventually, this should give you a clear image of the scalability trends within your company.
Limit the dynamic rate
Limiting the dynamic rate should allow you to push the limits of max allowable throughput for clients. As different requests create different loads, it’s a good idea to set thresholds for rate limits according to the API’s cumulative load. That way, a user can make multiple performant requests quickly without any rate limitations.
Creating a secure and scalable API architecture requires a number of actions. Some of them you’ll complete initially, while others demand continuous monitoring. Still, once you set everything in order, you can start looking forward to lucrative business prospects.
Related posts
When was the first presidential election in the US?
The election process in the world’s most powerful nation, the US, has come a long way. Various amendments have been made to the Constitution that allowed black men, white women and other disadvantaged groups to participate in the elections. Further amendments during the 60s and…
Tips & Trick For Healthy Glowing Skin
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nam laoreet, nunc et accumsan cursus, neque eros sodales lectus, in fermentum libero dui eu lacus. Nam lobortis facilisis sapien non aliquet. Aenean ligula urna, vehicula placerat sodales vel, tempor et orci. Donec molestie metus a sagittis…
My Fight With Depression. Concussions
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nam laoreet, nunc et accumsan cursus, neque eros sodales lectus, in fermentum libero dui eu lacus. Nam lobortis facilisis sapien non aliquet. Aenean ligula urna, vehicula placerat sodales vel, tempor et orci. Donec molestie metus a sagittis…
Top 10 most visited tourist places in the world
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Nam laoreet, nunc et accumsan cursus, neque eros sodales lectus, in fermentum libero dui eu lacus. Nam lobortis facilisis sapien non aliquet. Aenean ligula urna, vehicula placerat sodales vel, tempor et orci. Donec molestie metus a sagittis…
How Digital Health Technology Is Beneficial?
Digital health revolves around the usage of diverse technological platforms including mobile health, teen health, configurable remote patient monitoring, etc to improve the connection between the patients and the doctors. Across the healthcare system, the horizon and scope of digital health have helped create opportunities…
How Latest Farmtrac Tractors are Improving Farming in India?
India mostly relies on farming, and a large part of the population depends on it for their livelihoods. Recently, there’s been a big shift towards using modern farming techniques and machinery to make farming more productive and efficient. A good example of this is the…
Dispelling Myths: Demystifying Rx Waste and Expiration Dates – WasteX Pharmaceutical Waste Disposal Separates Fact from Fiction
The specter of “expired” medication looms large, conjuring images of potent chemicals wreaking havoc on water sources and ecosystems. But before you panic toss that bottle of pills, let’s delve into the truth about pharmaceutical waste and expiration dates, separating fact from fiction. At WasteX…
Sustainable Living in Memphis: Green Initiatives and Eco-Friendly Hotspots
Memphis, a city known for its rich cultural heritage and vibrant atmosphere, is increasingly becoming a hub for sustainable living. As environmental awareness continues to grow, residents and businesses in Memphis are embracing green initiatives and fostering eco-friendly practices. Let’s explore the city’s commitment to…
Today's pick
Hot topics
Stay connected
Meet the Author

Gillion is a multi-concept WordPress theme that lets you create blog, magazine, news, review websites. With clean and functional design and lots of useful features theme will deliver amazing user experience to your clients and readers.
Learn moreCategories
- Animals (7)
- Apps & Softwares (8)
- Automotive (8)
- Beauty (8)
- Business (141)
- Cars (12)
- Cartoon (3)
- Cook (4)
- Cooking (1)
- Design (8)
- Economy (6)
- EDUCATION (25)
- Entertainment (16)
- Fashion (23)
- Fitness (2)
- Food (16)
- Gaming (51)
- Guide (20)
- Health (119)
- Home (52)
- Home improvement (12)
- Interior (3)
- Law (16)
- Life (1)
- LifeStyle (99)
- Marketing (5)
- Motivation (9)
- Movie (6)
- Movies (1)
- Music (3)
- News (8)
- Painting Art (1)
- People (15)
- Photography (7)
- Review (113)
- Services (7)
- Social Media (6)
- Sport (9)
- Sports (12)
- Style (10)
- Swimming (1)
- Tech (125)
- Travel (26)
- Uncategorized (17)
- Vape (5)
- Western (3)
- World (2)